|
Legal Minds on Information Law |
Cat: ECO |
Koichiro Hayashi (林紘一郎) |
17609u/18227r |
Title |
Legal Minds on Information Law |
情報法のリーガル・マインド |
|---|---|---|
Index |
||
Tag |
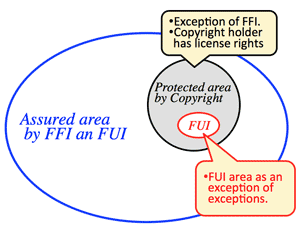
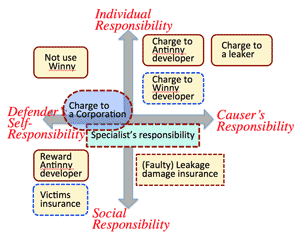
; ARP; Commitment responsibility; Contract & Trust; Creative Commons; Defamation; Fair Use (US); Forensic; Free & Secure; FUI; Civil Code (Jp); Classification of data; Classification of privacy (US); Google Books; Homo economicus; Injuction; LRA; Opt-out/in; Personal data & Privacy; Prior grant or post remedy; Privacy (US); Rechtsgut; Red team; Sarasohn & Protzman; Satisfice; Three layers of info.; Unregulation; | |
Résumé |
Remarks |
>Top 0. Preface:
|
0. 序文: |
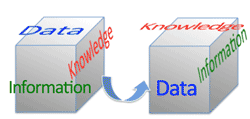
>Top 1. Features of information and its legislation:
|
1. 情報の特質と法のあり方
|
|||||||||||||||||||
|
||||||||||||||||||||
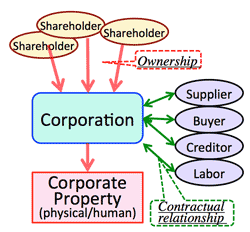
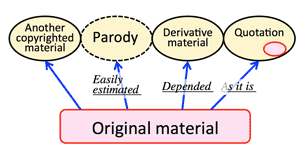
>Top 2. Information as an object of legal discipline:
|
2. 法的規律の対象としての情報:
|
|
|
|
|||
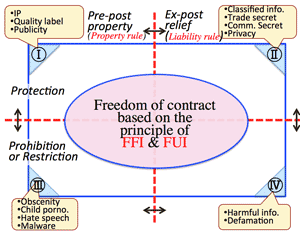
| Rule | Case of IP | Basis law | Efficacy |
1. Prior grant of rights, 事前の権利付与 |
Grant a license. Forbidding reproduction of the published work, without permission of the author. |
|
|
| 2. Regulation with injunction claims, 差止請求権付き行為規制 |
To prohibit the action which may injure profit of the creator, such as unauthorized reproduction |
|
|
| 3. Post remedy, 事後の利益救済 | Compensation in cash to the infringement of the right of the author intentionally or negligently. |
|
|
|
||||
| Category | Definition | Similar concept | Personal or Property | Remarks |
| 1. Right of self-determination, 自己決定権 |
Sexual preference; Give or give not birth to a baby |
Personal right; treated like property | Constitutional privacy | |
| 2. Betrayal of rational expectations of privacy, プライバシィの合理的期待裏切り |
Not to be intruded into virtual private space |
|
Personal right | Amendment 4 and 5 |
| 3. Trespass, 不法侵入 |
Not to be intruded into physical private space where others never interfere. |
|
Personal right | Spacial privacy |
| 4. Exposing private affairs, 私事の公開 | Not to be exposed what others should not know. |
|
Personal right | Ditto; Info. privacy |
| 5. Publication of misleading, 誤解を招く公表 |
Not to give misleading impression by exposing an certain info. |
|
Personal right | Ditto; Info. privacy |
| 6. Unauthorized use, 不正利用 |
The other makes a profit by using my name or affinity without permission. |
|
near Personal right | Ditto; is this also privacy? |
| 7. Right of publicity, パブリシティの権利 |
A public figure who has the right to merchandize his/her name, portrait, etc. | Property right (in US) |
Post (1991) clearly differentiate from 6. | |
|
|||||||
| Pattern | Public Goods 公共財 |
Governance Type 統治型 |
Transaction Type 取引型 |
Self- Realization Type 自己実現型 |
Medical Type 医療型 |
Criminal Investigation Type 犯罪捜査型 |
Internal Type 内面型 |
| Feature | accessible by anyone | collected by public force | collected through transaction | solicitation to the public | info. for medical treatment | info. for criminal investigation | one's thought and beliefs |
| Example | name, visage, *1 | tax, asset info. | bank account, electricity charges | name of author, stage name | medical records | fingerprint, voice print, DNA sequence | religious communion, sexual preference |
| Application | token *2 | control tag | marketing tool | token like | control tag marketing tool |
control tag | hidden token |
| Open /Secret *3 |
open | secret | open | open | secret | secret | secret |
| Personal dignity or Market differentiation | marketability | marketability | marketability | personal dignity, marketability |
personal dignity, marketability |
personal dignity | personal dignity |
| Risk of discrimination *4 | No | No | No | No | Yes | Yes | Yes |
| Remarks: |
|
||||||
>Top 3. Display of quality and guarantee:
|
3. 品質の表示と責任:
|
||||||||||||||||
|
|
||||||||||||||||
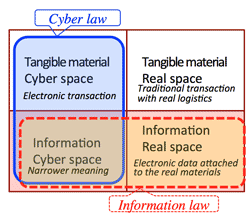
>Top 4. Future of the information law:
|
4. 情報法の将来:
|
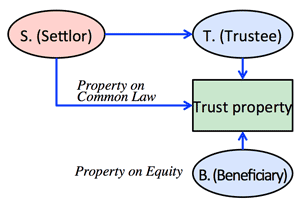
>Top Contract & trust |
Contract | Trust |
| Parties concern | Self-reliance and self-repsonsibility | Relationship between the strong (specialist) and the weak (non-specialist) |
| Legal obligation | Limited obligation | Prohibition of conflicts of interest. |
| Provision of information | Self-responsibility. Reciprocal confidentiality | Provision of information from the strong to the weak. Duty of confidentiality of trustee |
| Remedial measure | Compensation for damage | Disgorgement of profit, etc. |
| Freedom of content | Freedom of contract | Partly official intervention |
| Division of property | Not divided | Trust property is divided from other property. |
Comment |
|
|